Zero Trust Networks
Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access. This page gathers resources about the basic concepts of zero trust security, including a list of leading solutions.
Below we have compiled publicly available sources from around the world that present views on Zero Trust Networks.
The Container Security book by Liz Rice
Fundamental Technology Concepts that Protect Containerized Applications
Perspectives on Zero Trust Networks

Zero Trust Trends to Watch Out For in 2020
securityboulevard.com

2019 Was the Year of Zero Trust
avanan.com
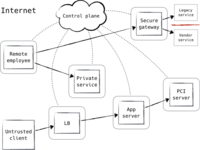
heimdalsecurity.com

What Is Zero Trust, and Why Does It Work?
comptia.org

Countdown to Zero: Why Zero Trust is in the Spotlight
securityboulevard.com

Zero Trust Networks: Best Practices To “Divide and Rule” Your Network
blog.checkpoint.com

The Zero Trust Approach for the Cloud
paloaltonetworks.com

Istio Security: Zero-Trust Networking
blog.aquasec.com

Zero Trust Networking – Death to the VPN
cloudreach.com

Network Security: Keys to Adopting Zero-Trust
securityboulevard.com

dzone.com

What is Zero Trust? A Security Model
varonis.com

csoonline.com

What is a Zero Trust Architecture?
paloaltonetworks.com

Zero Trust Security, What’s a Zero Trust Network?
cloudflare.com

4 Major Myths of Zero Trust Architecture
edge.siriuscom.com

Why You Should Embrace Zero Trust Networking
nojitter.com
How To

A Practical Guide to Zero-Trust Security
threatpost.com

3 Ways to Adopt Zero Trust Security Without Rebuilding Your Network
securityintelligence.com

A Guide to Planning Zero Trust Architectures
agileit.com

4 Easy Ways to Work Toward a Zero Trust Security Model
opensource.com

Implementing A “Zero Trust” Cyber security Approach
fedresources.com
Specific Technologies

How Zero Trust Security is Related to BeyondCorp
banyanops.com
Tools

akamai.com
Further Reading
Container Security Best Practices — When containerization is implemented with good security practices, containers can offer better application security rather than a VM only solution. This page gathers resources about basic tips, Docker security https://blog.aquasec.com/docker-security-best-practices best practices and Kubernetes security best practices.
Containers for DevSecOps — DevSecOps is an extension of the DevOps concept that emphasizes the integration of security teams into continuous delivery workflows. This page gathers resources about how DevSecOps makes for a more efficient and secure containers.
Container Vulnerabilities and Threats — While containers are driving evolution in the management of network applications, which, although self-contained, are still vulnerable. This page gathers resources about container vulnerabilities like ‘Dirty Cow’ and ‘Escape Vulnerability’ including tips on how to secure containers from cyber threats.
Container Vulnerability Scanning — A big part of any organization’s risk assessment process is to be aware of and gain visibility into vulnerabilities in the software being used. This page gathers resources about the the importance of container vulnerability scanning including Docker vulnerability scanning and information on various vulnerability scanners.
Container Secrets Management — In computing as in real life, a secret is information you want kept private, outside of the people and systems you want or need to share it with. In the application security realm, common examples of secrets are passwords, tokens, and private keys. This page gathers resources about managing secrets in containers including Docker containers, Amazon Elastic Container Service, Kubernetes and more.
Container Access Control — The wide adoption of containers and the ability to retrieve images from different sources impose strict security constraints. Containers leverage Linux kernel security facilities, such as namespaces, cgroups and Mandatory Access Control. This page gathers resources about container access control - deciding and enforcing who gets access to which container resources.
Container Audits and Compliance— Security and compliance are top of mind for IT organizations. In a technology-first era rife with cyber threats, it is important for enterprises to have the ability to deploy applications on a platform that adheres to stringent security baselines. This page gathers resources about audits and compliance of containers and their relationship to security.
Application Whitelisting— Whitelisting is the practice of specifying an index of approved applications that are permitted to be present and active. There are several characteristics of containers that lend themselves to intent-based security, which, in effect, is whitelisting. This page gathers resources about whitelisting in Kubertenes and other platforms.
Zero Trust Networks— Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access. This page gathers resources about the basic concepts of zero trust security, including a list of leading solutions.
Network Segmentation for Containers— Network segmentation is the practice of dividing a larger computer network into several small subnetworks that are each isolated from one another. This page gathers resources about the security benefits of network segmentation, the rise of micro-segmentation and the nano-segmantation approach.
Container Isolation— Container isolation aim to protect the underlying host OS that runs containers and functions against malicious escape and breakout attempts into other targets on the same host or on the shared infrastructure. They attempt to provide VM-level isolation while maintaining the expected speed and efficiency. This page gathers resources about isolation technologie such as Kata Containers, Amazon Firecracker, gVisor and Nabla Containers.
Open Source Security Tools for Containers—Open Source Security Tools for Containers — As containers becomimng more popular, the instances of malware are increasing. Securing containers is a top priority for DevOps engineers. This page gathers resources about open source security tools for containers such as: kube-bench, kube-hunter, Clair and more.
Open Source Vulnerability Scanner—A vulnerability scanner is an application that identifies and creates an inventory of all the systems connected to a network, and then checks each item in the inventory against one or more databases of known vulnerabilities to see if any items are subject to any of these vulnerabilities. This page gather resources about open source vulnerability scanners from various vendors.
Open Source Security Tools—Technology has come a long way, but so does hacking. Just like the digital world, hacking techniques and tools have also become more sophisticated and also threatening. This page gather resources about open source security tools for containers, websites, and software.
Container Security Tools—Containers have been one of the hottest trends in the software industry in recent years as more organizations turn to them to build. In working with containers, we need to recognize that they face a different range of threats from other sorts of software that we use. This page gathers resources about container security tools and compare them.













